Resource Profile:
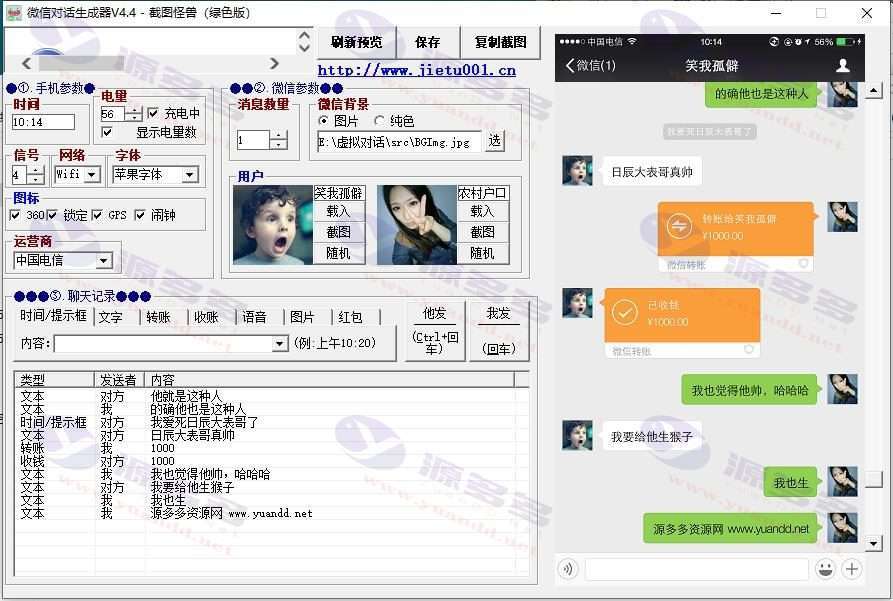
This program is a free to install WeChat chat interface generation tool, which can be run directly on Windows system computers. By simulating the real WeChat interface, users can customize a number of parameters to generate high-fidelity screenshots of the conversation, which is suitable for prototyping, visual design reference and other application scenarios.
Support features include:
Customizable phone system time, battery display, network signal, Wi-Fi status, chat background image, font style, carrier name (e.g. China Telecom), device icon and lock screen interface, etc.
In addition, it also supports editing conversation content, chat time, prompt bubbles, customizing sender nicknames and avatars, simulating voice messages, transfer messages, red packet records, system prompts and other elements, which is easy to operate and has a real effect.
Photo Gallery:
- Can free downloads or VIP member-only resources be commercialized directly?
- The resources on this site are collected and organized through the network, for personal research and study purposes only. The copyright belongs to the legal owner of the software and program code, users should verify the copyright and legality of the resources, prohibited for commercial use, illegal activities or any violation of national laws and regulations.
- Disclaimer of liability for program or code bugs, compatibility issues or functional defects, etc.
- As the resources on this site are collected and organized through the network, not the site's original, it can not fully guarantee its functionality or code compatibility. Users need to verify whether the resources meet the needs of their own, due to the following circumstances lead to losses, this site does not assume any responsibility:
Programs, source code and other computer software resources may contain code vulnerabilities (bugs), compatibility issues or functional defects left by the developer. This site does not provide free repair services for such technical defects, users need to bear the risk of debugging, modification or abandonment of the use.